

Zero Trust security can protect your software development projects by demanding verification before allowing access. Improve your cybersecurity with practical tips for implementing Zero Trust.
Imagine the latest secret agent blockbuster from Hollywood. A star like Tom Cruise or Daniel Craig surmounts walls, barbed wire, fences and doors with electric locks. Finally, he infiltrates the secret facility and the tension… drops… Because suddenly everything becomes very easy. Since he is within the secure area guards, personnel and security systems all assume he has legitimate access and trust him. Upon request, a janitor hands him a universal key card, and the hero walks comfortably out of the main entrance with all the secrets in his backpack…
Apart from the lack of suspense, this scenario would probably be too implausible even by Hollywood standards and would be rejected by audiences. After all, even at your own workplace you would be more suspicious of unusual activity than the guards in this imaginary film. If a complete and total stranger walks through your offices unannounced, you usually want to know what's happening and you wouldn't trust this person at first. Only a form of legitimization would rectify this problem.
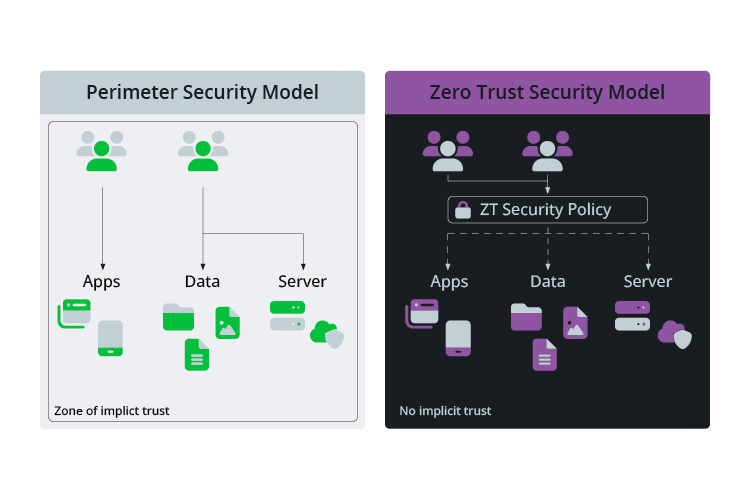
It is surprising that classic architectures for data security are usually built according to this principle of perimeter security, and even more so that new software projects are also often still designed in this way. Once a device, software or user is within the secure area of a network, legitimation is no longer required. Intruders can look around, gain access to other areas or even send data outside the network.
However, this is increasingly being contrasted with a principle of security architecture which is based on the philosophy of "Never trust anyone or anything." The buzzword here is "Zero Trust". This security approach should be standard for the implementation of all digitization projects, but unfortunately, we are still a long way off. Any organization that builds software systems should consider the principles of "Zero Trust" for their projects to effectively minimize the risks of cyberattacks and data theft.
Zero Trust is a security concept based on the assumption that threats can come from both the outside and the inside. It does not rely on traditional security approaches, which are often based on the principle of "trust, but verify". Instead, Zero Trust maintains constant suspicion and verifies every request as if it had come from an unsecured network, regardless of its origin. There is no longer a distinction between "inside the network" or "outside the network" when exchanging data, there is only "verified" or "not verified". Additionally, verification is valid for a limited time only and needs to be confirmed on a regular basis. "Trust" is therefore constantly being checked dynamically based on guidelines and risk analyses.
The concept is based on several core principles:
As digitization progresses, it becomes ever more important to protect IT systems. However, as more data, business processes and transactions are digitized, the challenges created by this progress keep growing. Digitization increases potential attack surfaces, as well as the complexity of the systems. The Zero Trust approach helps to meet these challenges.
There is no patent recipe for implementing the principles of "Zero Trust" in your own IT landscape. Rather, you must first analyse your systems in detail and then create a suitable security concept which aligns with "Zero Trust".
Although Zero Trust is unfortunately still not the predominant security architecture in the IT industry, cronn has already implemented several projects for companies and government agencies with Zero Trust architectures. The latter in particular handle sensitive personal data of citizens and must meet the highest security standards. Our teams have already proven their expertise to ministries and authorities at state level and have consistently designed corresponding projects according to this approach.
We will be happy to outline the requirements for your project or advise you on existing and planned projects in areas of data security and security architecture. After that, we can plan measures and projects with you. Depending on your needs, we can support you in the implementation, or take over the entire project for you.
